Domain Verification Setup
To engage customers through email marketing, you need to include domain authentication methods. These methods increase your sender reputation and deliverability, allowing your bulk emails to pass inbox providers’ spam filters.
There are three main methods: SPF, DMARC, and DKIM. They are usually implemented as TXT (a type of DNS record in legible text form) records in your domain’s DNS settings.
All three records should be included to ensure the highest email security and deliverability.
SPF (Sender Policy Framework)
SPF record contains a list of all the authorized email providers that can send emails using your domain. The receiving inbox provider analyzes your SPF record to see if the sender is authorized by your domain.
Setup
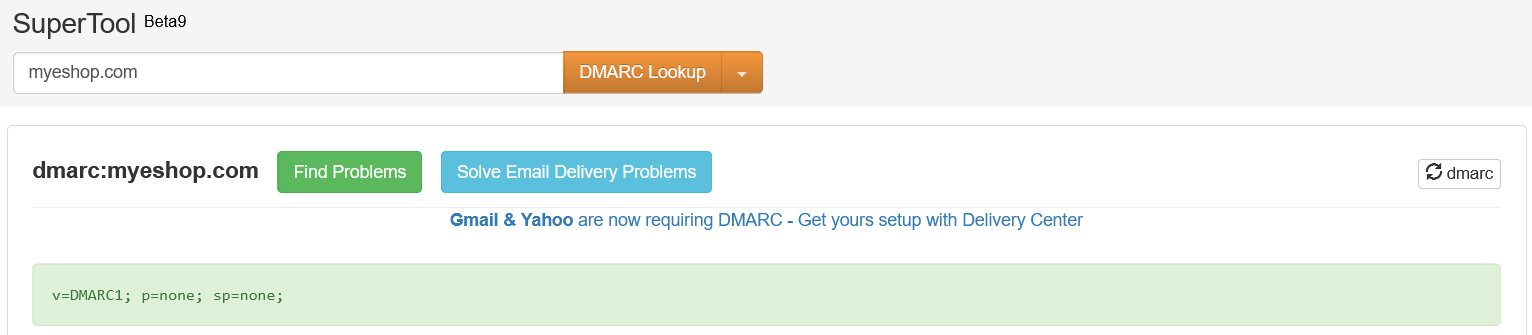
Here is the guide to setting up an SPF record on the “myeshop.com” domain. SPF settings (as DKIM and DMARC) are highly provider-dependent, but the general process goes as follows:
Access your DNS settings and create/edit your SPF record. If there already is an SPF record, look for: “v=spf1”. An SPF record looks like this:
To add a cortex email provider, simply add your ESP with the “include” statement. The resulting record for the cortex domain should look like this:
Even though you use multiple providers, you need to have only one SPF record!
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC establishes a domain policy to deal with emails that fail DKIM and/or SPF checks. Therefore, in order to have a functioning DMARC record, you need both DKIM and SPF records.
Including a DMARC record in your DNS is highly advised. Some inbox providers (most notably Google) require a DMARC policy for the sender’s marketing emails to pass their spam filter.
Setup
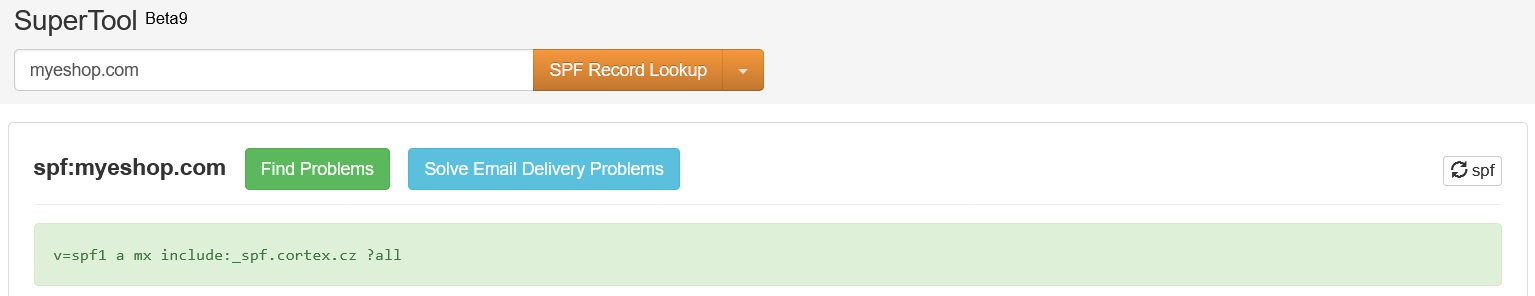
Here is a guide to setting a DMARC record for the “myeshop.com” domain:
Access your domain’s DNS settings.
Create a TXT record in your DNS. An example looks like this:
| Name | Type | Content | ||
|---|---|---|---|---|
| _dmarc.example.com | TXT | v=DMARC1; p=none; sp=none; |
“example.com” stands for your domain, “p” can be set to:
- p=none (even if “your” email fails DKIM and SPF checks, you still recommend sending it)
- p=quarantine (if the email fails the checks, it should go to spam)
- p=rejection (if the message fails the checks, you are advised to reject it)
- “sp” specifies the handling of the policy by all your subdomains
To properly set up DMARC policy for the cortex domain, the record follows:
DKIM (DomainKeys Identified Mail)
DKIM works as an encrypted digital signature in the email’s header. It is verified by a DNS record with two parameters: decryption key and selector. Upon receiving your email, the receiver ESP extracts a public decryption key from your DNS. If the key works and the signature is decrypted, the email passes the DKIM validation check.
Setup
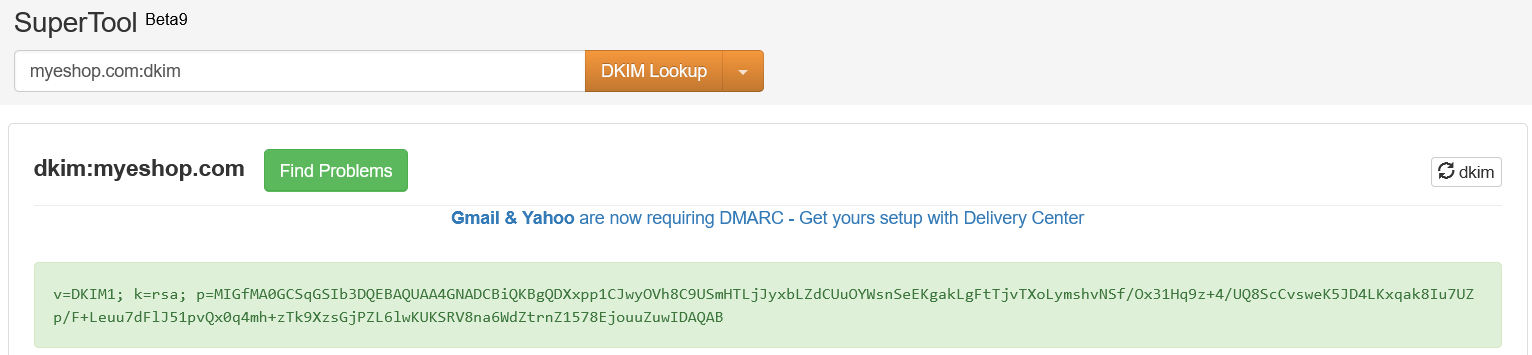
Here’s the guide to setting up a DKIM record for the “myeshop.com” domain:
Add a new DNS record of type CNAME with next value dkim._domainkey.myeshop.com and alias dkim._domainkey.cortex.cz
Where myeshop.com should be replaced by your domain, that you will use for sending emails.
Set TTL to 6000.
alias: dkim._domainkey.cortex.cz
where myeshop.com is your domain name.
Once you set your DKIM record, reach out to your project manager. We must confirm and set the domain name on our side to correspond!
If you plan to send emails from multiple domains, you must repeat this procedure for each domain.
Final Note
These three records get your email message “accepted” by receiving providers, but they do not necessarily deliver it to the inbox. Many different spam filters scan and evaluate your email content afterward.
You can check the correct settings here.
Below you can see how it should look like.
Enter your domain name and select SPF from the dropdown.
Enter your domain name and select DMARC from the dropdown.
Enter your domain name, after the domain name insert :dkim and select DKIM from the dropdown.